Ssh Generate Host Dsa Key
SSH keys follow conventional asymmetric authentication schemes: a keypair, consisting of a public and private key, is generated (saved, by default in the.ssh/idrsa and.ssh/id-rsa.pub files on the client) and the public key is sent to the destination host. When the client tries to authenticate it signs the request with the private key and the. Oct 05, 2007 ssh-keygen can generate both RSA and DSA keys. RSA keys have a minimum key length of 768 bits and the default length is 2048. When generating new RSA keys you should use at least 2048 bits of key length unless you really have a good reason for using a shorter and less secure key.
How to Generate a Public/Private KeyPair for Use With Solaris Secure Shell
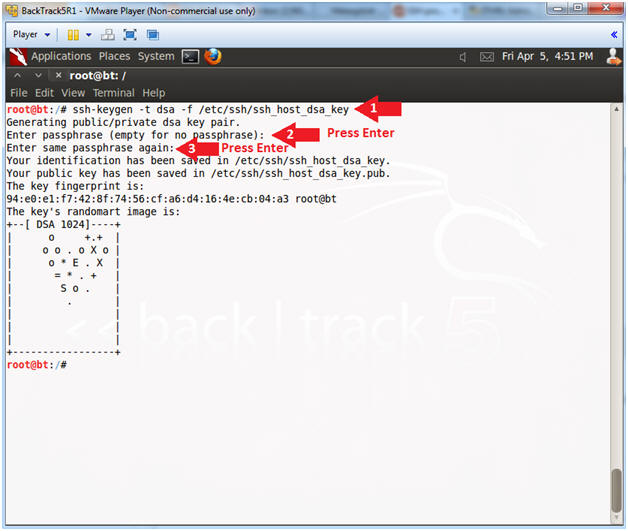
Users must generate a public/private key pair when their site implementshost-based authentication or user public-key authentication. For additionaloptions, see the ssh-keygen(1) manpage.
Before You Begin
Determine from your system administrator if host-based authenticationis configured.
Start the key generation program.
where -t is the type of algorithm, one of rsa, dsa, or rsa1.
Specify the path to the file that will hold the key. Openssl rsa public key.
Bydefault, the file name id_rsa, which represents an RSAv2 key, appears in parentheses. You can select this file by pressing the Return key. Or, you can type an alternative file name.
The file name of the public key is created automatically by appendingthe string .pub to the name of the private key file.
The serial number for Nero is available This release was created for you, eager to use Nero 7 full and with without limitations. Our intentions are not to harm Nero software company but to give the possibility to those who can not pay for any piece of software out there. Serial means a unique number or code which identifies the license of the software as being valid. All retail software uses a serial number or key of some form. A serial number can also be referred to as an Activation Code or CD Key. When you search for Nero 7.11.6.0 Serial, you may sometimes find the word 'serial' in the results. SERIAL NUMBER NERO 7. CD KEY NERO 7. Nero 7 serial number key generator. Nero 7 Premium Serial Number + Crack Full Version Free Download. Nero 7 Serial Number. Nero 7 Premium Serial Number with Crack is the world's best software pack. It includes tools to burn DVDs, Edit videos, Create disc image files, Edit audio files, share videos or all format of files. Jan 25, 2017 NERO 7 Premium Serial Number. 1C82-0000-19E5-MAAX-4008-3107-5146 1C82-0000-19E5-MAAX-4005-1132-7307 1C82-0000-19E5-MAAX-4003-4800-6391. NERO 7 Essential Serial Number. 1C82-0000-19E5-MAAX-4001-4287-0355 1C82-0000-19E5-MAAX-4005-1233-3675. Special Screhnshots: Download Nero 7 Premium Serial Number + Crack Full Version From Links Given Below.
Type a passphrase for using your key.
This passphraseis used for encrypting your private key. A null entry is stronglydiscouraged. Note that the passphrase is not displayed when youtype it in.
Retype the passphrase to confirm it.
Check the results.
Check that the path to the keyfile is correct.
At this point, you have created a public/private key pair.
Choose the appropriate option:
If your administrator has configuredhost-based authentication, you might need to copy the local host's publickey to the remote host.
You can now log in to the remote host.For details, see How to Log In to a Remote Host With Solaris Secure Shell.
Type the command on one line with no backslash.
When you are prompted, supply your login password.
If your site uses user authentication with public keys, populateyour authorized_keys file on the remote host.
Copy your public key to the remote host.
Type thecommand on one line with no backslash.
When you are prompted, supply your login password.
Whenthe file is copied, the message “Key copied” is displayed.
(Optional) Reduce the prompting for passphrases.
For a procedure, see How to Reduce Password Prompts in Solaris Secure Shell. For more information, see the ssh-agent(1) and ssh-add(1) man pages.
Example 19–2 Establishing a v1 RSA Key for a User

In the following example, the user cancontact hosts that run v1 of the Solaris Secure Shell protocol. To be authenticated by v1hosts, the user creates a v1 key, then copies the public key portion to theremote host.