Openvpn Server Generate Client Keys
At the prompt, change the Common Name to your client's domain name using the format client2.example.com. Leave all of the remaining fields as the default values.
- With a bit more effort, we could have done this differently. For example, instead of generating the client certificate and keys on the server, we could have had the client generate its own private key locally, and then submit a Certificate Signing Request (CSR) to the key-signing machine.
- Oct 20, 2017 It is possible to generate your certificates on the router itself if you don't have access to a Linux machine, or if you don't have a Windows client installed with Easy-RSA. Easy-RSA is a simple to use environment that is bundled with OpenVPN, and has been included in Asuswrt-Merlin. Setting up the environment.
- Aug 22, 2016 I installed OpenVPN on a Ubuntu machine, and generated certificates to allow another Linux client to connect. Verified it's working, and the client is forced to use the VPN tunnel. In the example I followed, the server certs (including the DH pem file) were moved to /etc/openvpn. Client certs were moved elsewhere.
- Jun 30, 2016 This is a demo on how to generate server and client certificate for OpenVPN. This is a demo on how to generate server and client certificate for.
- Step 3 - Build OpenVPN Keys. In this step we will build the OpenVPN keys based on the easy-rsa 3 & # 39; file that we created. We will build the CA key, server and client keys, DH and the CRL PEM file.
Important: If you don't follow the format specified above for setting common names, the domain names aren't available when you import the certificate into ACM. As a result, the certificate isn't an available option for specifying the server certificate or client certificate when you create the AWS Client VPN endpoint.
Choose a system to act as your CA and create a new PKI and CA:./easyrsa init-pki./easyrsa build-ca 2. On the system that is requesting a certificate, init its own PKI and generate a keypair/request. Note that the init-pki is used only when this is done on a separate system (or at least a separate PKI dir.) This is the recommended procedure.
Import the server and client certificates and keys into ACM
Note: The server and client certificates, and their respective keys, are available in C:Program FilesOpenVPNeasy-rsakeys.
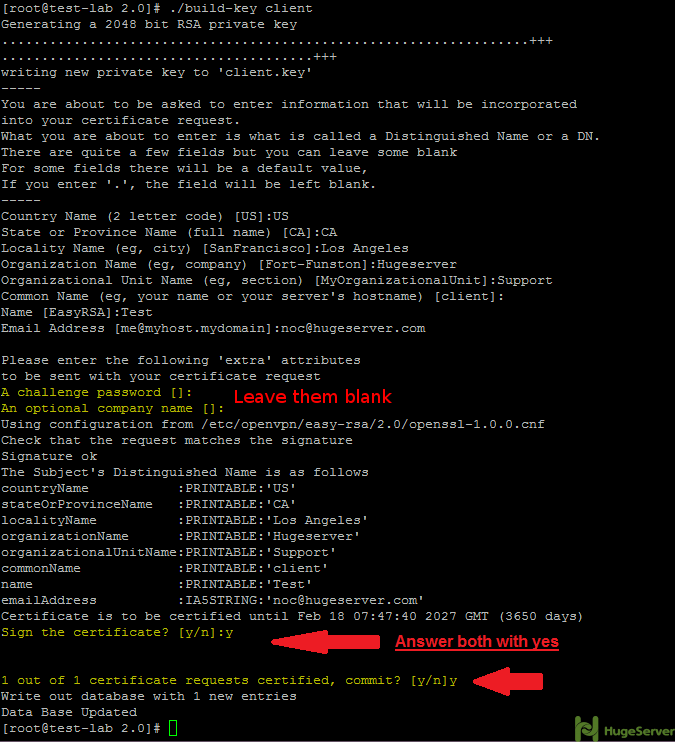
1. Open the following files: server.crt, server.key, client1.crt, client1.key, and ca.crt.
2. Open the ACM console, and then choose Import a certificate.
3. On the Import a certificate page, copy/paste the content:
From the server.crt file to Certificate body.
From the server.key file to Certificate private key.
From the ca.crt file to Certificate chain.
4. Choose Import to import the server certificate.
Openvpn Server Generate Client Keys Download

5. Choose Import a certificate again and copy/paste the content:
From the client1.crt file to Certificate body.
From the client1.key file to Certificate private key.
From the ca.crt fileto Certificate chain.
Generate Openvpn Keys
6. Choose Import to import the client certificate.
Openvpn Connect Client
Or, you can use the AWS Command Line Interface (AWS CLI) to import the server and client certificates and their keys into ACM:
WPA2 implements the full standard, but will not work with some older network cards. WPA is designed to work with all, but not necessarily with first generation. They were created in response to several serious weaknesses researchers had found in the previous system, (WEP). WPA implements the majority of the standard, and was intended as an intermediate measure to take the place of WEP while 802.11i was prepared. Wpa2 aes based ccmp encryption. Both provide good security, with two significant issues:.